Protect the ESXi virtual machines with OpenBSD
813 words, 4 minutes
I own a server at Online.net which now runs VMware ESXi free edition. The thing is VMs have to access the Wild Wild Web and provide public services while still being protected. So let’s configure OpenBSD to do so.
The big picture
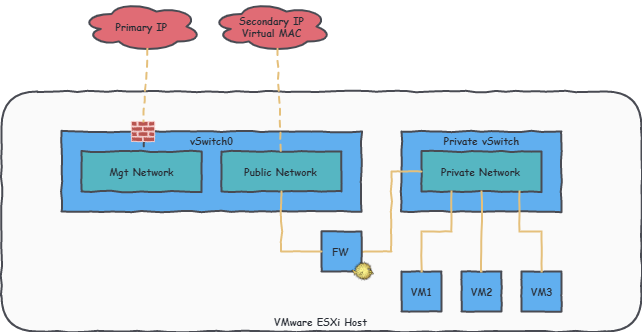
As explained in the Online.net documentation, the hypervisor will keep its primary address for (management) services ; maybe you want to protect it a bit . An extra fail-over IP and virtual MAC can be purchased to gain Internet access to the hosted virtual machines. The VMs will be protected for the wilds using an OpenBSD virtual machine.
Purchase an extra IP
From the Online.net user interface, buy a fail-over IP. Affect this IP as a secondary IP for the ESXi server. Add a virtual MAC address to the secondary IP.
Write down the IP and MAC. They’ll be used by the OpenBSD virtual machine.
Configure the ESXi network
I configured the ESXi vSwitch, port groups etc using SSH. Because I have enabled SSH, because it is possible and because it is easier to script ; should you need to apply the whole configuration from scratch… This can also be done via the Web Interface ; I won’t detail that path here.
First of all, I rename the default VM port group so I can identify it easily:
# esxcfg-vswitch -D "VM Network" vSwitch0
# esxcfg-vswitch -A "Public Network" vSwitch0
Then I create a dedicated vSwitch to store my LAN virtual machines:
# esxcfg-vswitch -a "Private vSwitch"
# esxcfg-vswitch -A "Private Network" "Private vSwitch"
Finally, I sync the configuration with the persistent storage and have the vSphere Web Client aware of that configuration.
# vim-cmd hostsvc/firmware/sync_config
# /etc/init.d/hostd restart ; /etc/init.d/vpxa restart
In my testings, the vSphere Web Client wouldn’t show the vSwitch and Port Group modifications if not reloaded. Furthermore, the ESXi lost the configuration on reboot if not manually synced.
Create the OpenBSD firewall VM
From the vSphere Web Client, browse to https://<primary_ip>/ui/#/host/vms and create a new virtual machine.
- Compatibility = ESXi 6.7 virtual machine
- Guest OS family = Other
- Guest OS version = “FreeBSD Pre-11 versions (32-bit)”
Selecting FreeBSD makes the ESXi happy with OS identification. One can use “Other” but “Status” will end in “Warning” mode rather than “Normal”.
The virtual machine will have two virtual NICs. The first one is linked to the “Public Network” and requires the virtual MAC from the previous step. The second one is simply linked to the “Private Network”.
- Network Adapter 1
- Port Group = “Public Network”
- Adapter Type = “VMXNET 3”
- MAC Address = “Manual”
- MAC Address value =
- Network Adapter 2
- Port Group = “Private Network”
- Adapter Type = “VMXNET 3”
Upload the OpenBSD installation ISO to a datastore, attach it to the VM and boot to run the installation program.
Installation specifics
The OpenBSD virtual machine will use the secondary IP address as its public IP. But the default gateway has to be configured to be the primary IP address of the ESXi host. Both not being part of the same network, there is a need to create a static network route.
The installation process will be paused to create the network route.
(...)
Which network interface do you wish to configure? vmx0
>
Netmask for vmx0? 255.255.255.255
(...)
Default IPv4 route? !
# > -llinfo -link -static
# exit
>
(...)
Apply that configuration to the installed VM. Either by modifying the files on the disk before rebooting. Or by configuring the network from the virtual machine console on reboot.
# cat /etc/hostname.vmx0
inet <em><secondary_ip></em> 0xffffffff
!route add -inet <em><primary_ip></em> -llinfo -link -static -iface vmx0
!route add default <em><primary_ip></em>
# cat /etc/hostname.vmx1
inet <em><private_ip></em> 0xffffff00
group lan
Routing and Filtering
Building an OpenBSD router is detailed in the PF section of the FAQ . You shall now read it (again) to complete the configuration. You may also read the great Network Management with the OpenBSD Packet Filter Toolset tutorial.
In my case, the virtual machine will host a dhcpd(8) so that the testing VMs easily get IPs, an httpd(8) server to allow internal autoinstall for other OpenBSD VMs, an unbound(8) and ntpd(8) for the whole LAN and a relayd(8) to publish services from the LAN to the Internet. pf(4) limits what can come into the LAN and what can go out of it. Read the man pages to configure each of those.
It would be possible to add extra vNIC and vSwitch to implement DMZ, staging networks and “workstation” zones.
I have configured ESXi to autostart a bunch of VMs. But I also have configured the router VM with an encrypted disk. Which means that on reboot, nothing shall go in or out of the LAN until I enter the passphrase. Consider this pros/cons is up to you.
🐡 If you went that far, you have no excuse now to continue running pfSense on your ESXi 😈