Quick overview on Synology Directory Server
567 words, 3 minutes
Quoting the Package Center description: “Directory Server provides LDAP service with centralized access control (…)”.
Let’s have a (quick) look at what Synology’s LDAP service provides.
Service installation
The first thing to do is to enable the service.
From the Package Center, browse to the “Utilities” section and select “Directory Server”. Click the “Install” button and let it flow. In this example, I’ll use version 1.1-2215 from DSM 4.2 ; still on my DS409slim. The installation is really straightforward and, in the end, you’ll get a “Directory Server” icon in the Start menu.
Click the “Enable LDAP Server” checkbox and fill-in the FQDN followed by the “administrative” password for the LDAP server. When click “Apply”, you’ll be prompted if “you want to configure the client settings to bind to this server with default settings”. For the fun, I answered “Yes”.
What is not clear from the help system is that the “FQDN” will be mapped into the “Base DN”. In my case, I used “FQDN: tumfatig.net” which led to the creation of the following data:
dn: dc=tumfatig,dc=net
dn: cn=users,dc=tumfatig,dc=net
dn: cn=groups,dc=tumfatig,dc=net
dn: cn=synoconf,dc=tumfatig,dc=net
dn: cn=MinID,cn=synoconf,dc=tumfatig,dc=net
dn: cn=MaxID,cn=synoconf,dc=tumfatig,dc=net
dn: cn=CurID,cn=synoconf,dc=tumfatig,dc=net
dn: cn=MaxNum,cn=synoconf,dc=tumfatig,dc=net
dn: sambaDomainName=tumfatig,dc=tumfatig,dc=net
dn: cn=users,cn=groups,dc=tumfatig,dc=net
dn: cn=Directory Operators,cn=groups,dc=tumfatig,dc=net
dn: cn=administrators,cn=groups,dc=tumfatig,dc=net
dn: uid=admin,cn=users,dc=tumfatig,dc=net
Users and groups management
Groups will be named and provided with a description. They will be then filled with usernames. Nothing more, nothing less.
Users are created or imported and benefits from the inetOrgPerson LDAP Object Class.
From the technical point of view, a user is built on:
objectClass: top
objectClass: posixAccount
objectClass: shadowAccount
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: apple-user
objectClass: sambaSamAccount
objectClass: sambaIdmapEntry
objectClass: extensibleObject
The matches go like this:
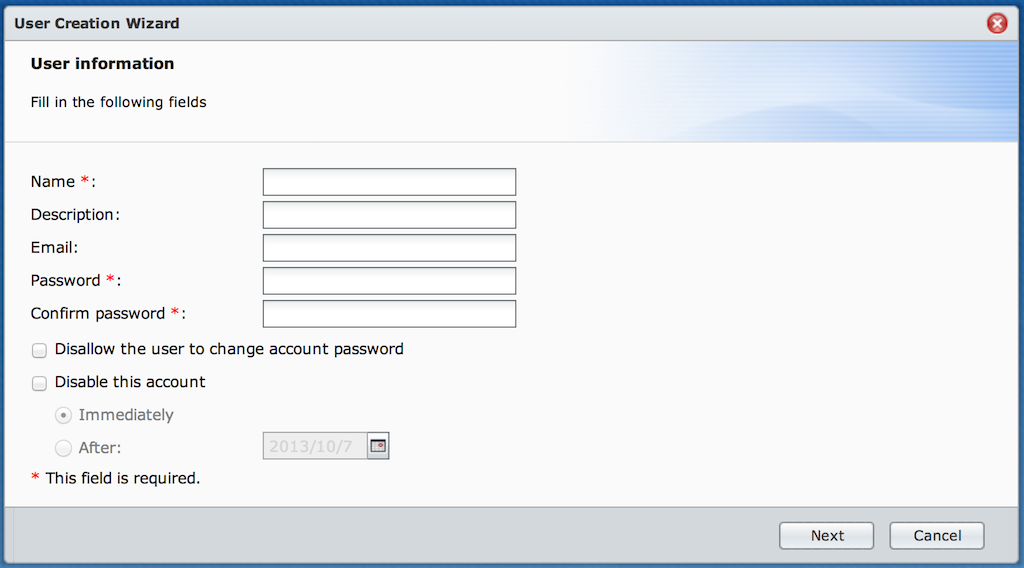
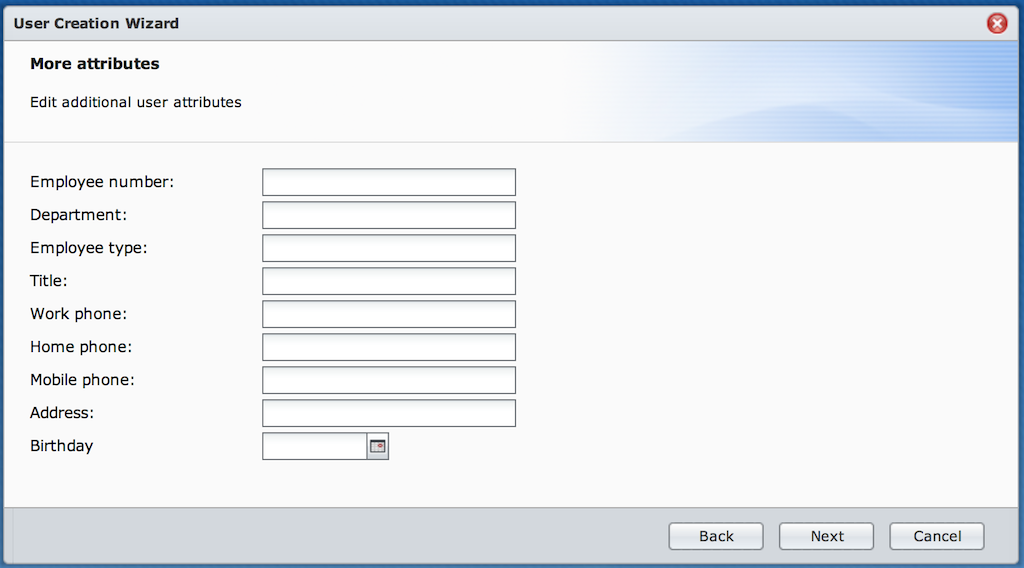
- “Name” matches uid, cn, sn and displayName properties ;
- “Description” matches gecos ;
- “Email” matches the mail property ;
- “Password” matches userPassword ;
- “Disable this account” matches the shadowExpire and shadow* properties ;
- “Birthday” matches apple-birthday ;
- “Mobile phone” matches mobile ;
- “Department” matches departmentNumber ;
- “Employee number” matches employeeNumber ;
- “Employee type” matches employeeType ;
- “Home phone” matches homePhone ;
- “Address” matches postalAddress ;
- “Work phone” matches telephoneNumber ;
- “Title” matches title.
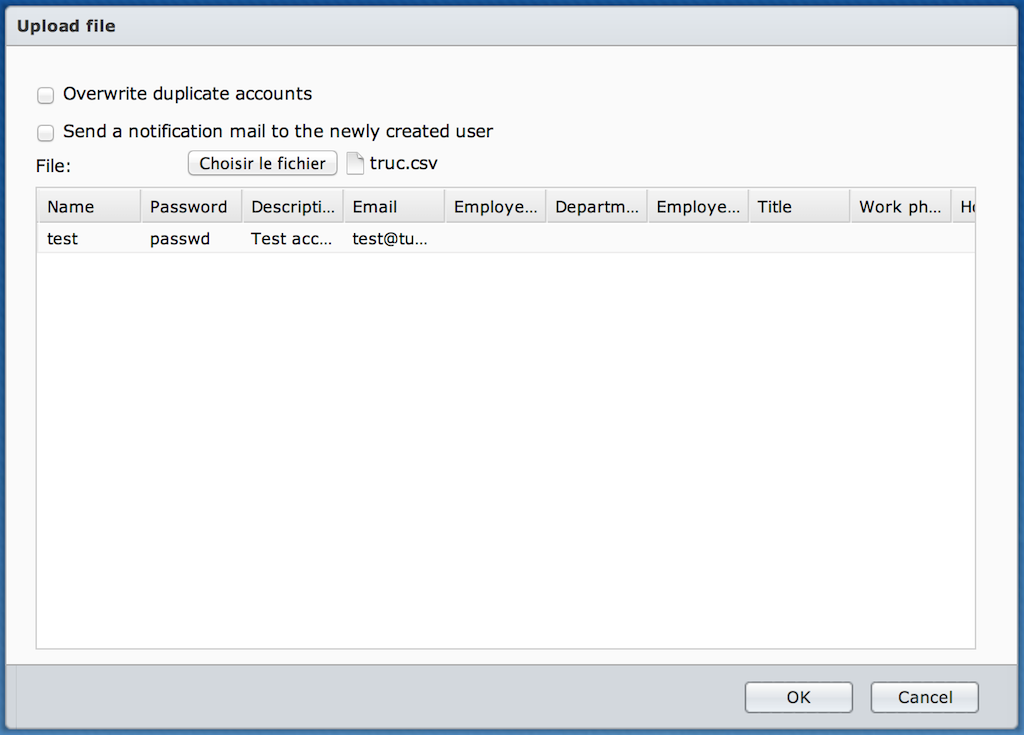
Rather than creating users by hand, you can import a CSV file. It must be filled-in with tab-separated data. During import, you’ll be able to match a particular column with a property.
Backup and restore
There is a nice backup feature that can be scheduled to run automatically. It can save a binary dump of the LDAP service in some local directory of the Synology. Yes, a binary dump… So you can’t use it straight from an external ldapadd…
Another thing
All in all, the Synology Directory Service is really simple to use and quite complete ; as soon as you only need a small directory.
Since you’ll need extra organisationUnit, you seem to be stuck. As far as I understood it, you cannot create various OU (to reflect an organization) and affect users throughout the LDAP tree. But since you only need to store a few users for various application authentication, that’ll do the trick.
Another thing that would have been great is the ability to work as a master/slave. Since the directory is the central point of authentication, it can also be a single point of failure… Synchronizing the data with another Synology, or an OpenLDAP server, would be a great option.
That all Folks! Now I need to check if OpenSMTPD can connect to it :p